Your cart is currently empty!
SQL Injection in Perspective of Ethical Hacking
Learn SQL Injection (SQLi), a critical web vulnerability. Discover its types, risks, and how ethical hackers use it to secure systems and protect Data.
SQL Injection (SQLi) is one of the most common and dangerous vulnerabilities in web applications. From an ethical hacking perspective, identifying and mitigating SQL Injection is a crucial part of securing systems and ensuring data integrity. This article explores SQL Injection, its types, the risks it poses, and how ethical hackers use it responsibly to uncover vulnerabilities.
What is SQL Injection?
It is a method where hackers insert harmful code into web apps by messing with SQL queries sent to a database. When apps don’t check user inputs bad guys can sneak in nasty SQL code to:
- Get into databases without permission.
- Grab, change, or wipe out important info.
- Do admin stuff in the database.
- Run commands on the computer system itself.
For good-guy hackers, checking for SQLi is part of their job to find weak spots before the bad guys can use them to cause trouble.
How SQL Injection Works?
At its core, SQL Injection occurs when a web application concatenates user inputs directly into SQL queries. For example, consider the following vulnerable query:
SELECT * FROM users WHERE username = '" + user_input + "' AND password = '" + pass_input + "';If an attacker enters the following input:
user_input = admin' --pass_input = anythingThe query becomes:
SELECT * FROM users WHERE username = 'admin' --' AND password = 'anything';Types of SQL Injection
Ethical hackers must be familiar with different types of SQL i techniques:
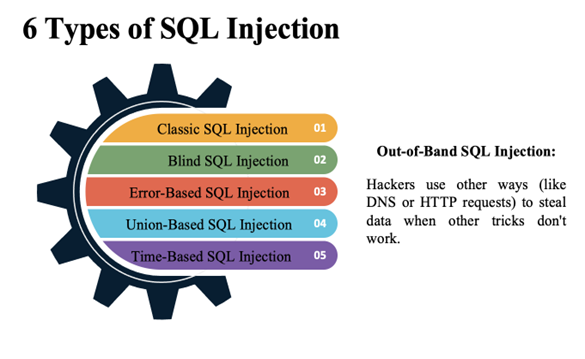
- Classic: Attackers insert SQL code into input fields to change queries.
- Blind: When apps don’t show SQL errors, hackers guess info by watching how the app acts (like how fast it responds or if pages change).
- Error-Based: Hackers use database errors to find out how the database is set up.
- Union-Based: Hackers use SQL’s UNION command to mix results from different queries and get data.
- Time-Based: Hackers add time delays to check if a query works.
- Out-of-Band: Hackers use other ways (like DNS or HTTP requests) to steal data when other tricks don’t work.
Risks of SQL Injection
SQLI poses severe risks to organizations, including:
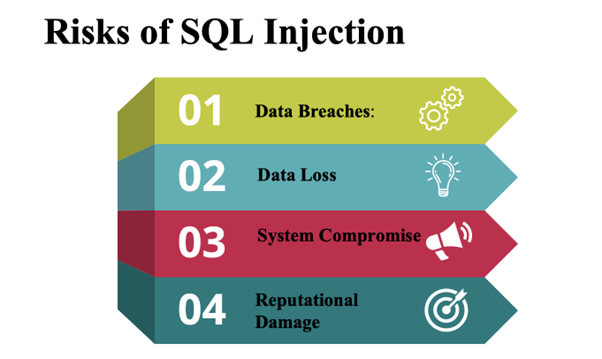
- Data Breaches: Exposure of sensitive information such as customer details, passwords, and financial records.
- Data Loss: Attackers can delete or alter critical data.
- System Compromise: Gaining administrative privileges can lead to full control of the database and even the underlying server.
- Reputational Damage: Breaches can harm the trust and reputation of businesses.
Ethical Hacking Approach to SQL Injection
Security experts uses this to spot weaknesses and suggest ways to fix them. A careful approach to ethical hacking involves:
- Scoping out: Mapping how the app works to find input fields, forms, and API endpoints that talk to the database.
- Checking for SQLi: Using hands-on methods and tools like SQLMap, Burp Suite, and Nmap to check for SQL Injection weak spots.
- Confirming and Testing: Making sure weak spots exist without hurting the database. o Ethical hackers try to show risks while avoiding any disruption.
- Writing it up: Giving detailed reports with proof of concept (PoC) and steps to recreate the weak spot. Suggesting ways to secure the app.
Mitigation Strategies
Ethical hackers emphasize the following best practices to mitigate SQL Injection risks:
- Input Validation:
- Validate and sanitize all user inputs to ensure only expected data is processed.
- Parameterized Queries:
- Use prepared statements with parameterized queries to separate SQL logic from user inputs.
Example in Python with SQLite:
cursor.execute("SELECT * FROM users WHERE username = ? AND password = ?", (username, password))- Use of ORMs:
- Object-relational mapping (ORM) frameworks like SQLAlchemy or Hibernate minimize the risk of direct query manipulation.
- Least Privilege Access:
- Grant the database only the permissions required for the application to function.
- Error Handling:
- Avoid displaying database errors to users; log errors internally instead.
- Regular Penetration Testing:
- Perform periodic penetration tests to identify and fix vulnerabilities.
Tools for SQL Injection Testing
Ethical hackers commonly use the following tools to test for SQL Injection vulnerabilities:
- SQLMap: A powerful automated tool for detecting and exploiting SQLi vulnerabilities.
- Burp Suite: A comprehensive web vulnerability scanner.
- Havij: A user-friendly SQLi exploitation tool.
- Nmap: For network reconnaissance and identifying potential vulnerabilities.
- OWASP ZAP: An open-source tool for identifying common security vulnerabilities, including SQLi.
Take away
SQL Injection remains a prominent threat in the cybersecurity landscape. From an ethical hacking perspective, understanding, identifying, and mitigating SQLi vulnerabilities are critical components of securing web applications. Ethical hackers play a vital role in protecting organizations by responsibly uncovering weaknesses and providing actionable solutions. By adopting best practices and leveraging advanced tools, SQLi risks can be significantly minimized, ensuring robust data protection and application security.
What is SQL Injection in ethical hacking?
It is a technique where malicious SQL code is injected into web applications to manipulate database queries. Ethical hackers identify such vulnerabilities to secure systems and prevent data breaches.
Why is SQL Injection dangerous?
It allows attackers to gain unauthorized access to sensitive data, delete or alter information, and even take control of the database server.
How do ethical hackers test for SQLi?
Ethical hackers test by submitting payloads in user inputs and observing responses. Tools like SQLMap, Burp Suite, and OWASP ZAP assist in automating the process.
What are some tools used to detect SQL-Injection?
SQLMap
Burp Suite
Nmap
Havij
OWASP ZAP
What is the role of ethical hackers in SQL Injection testing?
Ethical hackers identify the vulnerabilities, demonstrate the associated risks, and provide actionable solutions to strengthen application security.
Can SQLI be completely prevented?
While no system is 100% secure, following best practices like input validation, parameterized queries, and regular security testing can effectively prevent it.


