Your cart is currently empty!
A Beginner’s Guide to Cybersecurity: How to Protect Yourself Online
Discover the essentials of cybersecurity in this beginner’s guide. Learn how to protect yourself online from hacking, malware, and phishing in 2025’s digital age.
Technology in today’s world is messy. Cybersecurity is a bigger concern than ever in our digital world. Every aspect of our lives is linked to the internet, from social media to online banking. With this convenience, however, comes much risk! This is why it is now very critical that you understand the basic concepts, even if you are new to this exciting field. So, now let us get into the basics of Cybersecurity.
What Is Cybersecurity?
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These threats can come in various forms; such as hacking, malware, or phishing attacks and they can target both individuals and organizations. The goal of cybersecurity is to ensure the confidentiality, integrity of systems, and availability of digital information.
Key Words in Cybersecurity?
To begin, here are some basic words every beginner should learn:
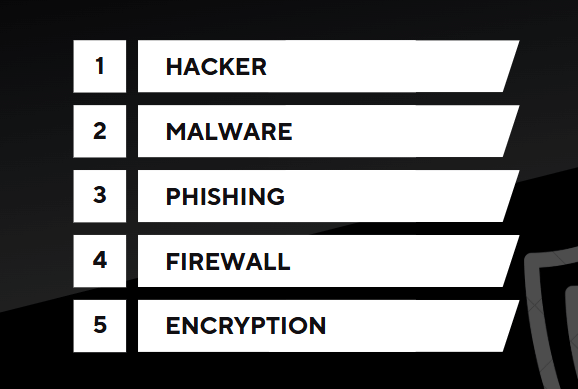
- Hacker:
- A person who uses technical abilities to get unauthorized access to systems or information.
- There are 3 categories in which we can list down hackers. Below are their types with a brief explanation:
- White Hat: Ethical hackers aiding in system security.
- Black Hat: Harmful hackers taking advantage of vulnerabilities.
- Grey Hat: Hackers operating between ethical and unethical lines.
- Malware:
- Malware is the short form for “Malicious Software”. It includes viruses, worms, ransomware, and spyware.
- Malware is generally used to steal, harm, or encrypt information.
- Phishing:
- Phishing is a type of cyberattack where the attackers trick individual into revealing sensitive personal information, such as passwords or credit card numbers, usually through fake emails or websites.
- Firewall:
- A security system that monitors and controls incoming and outgoing network traffic based on predefined rules.
- Acts as a barrier between trusted and untrusted networks.
- Encryption:
- A method of converting information into a code to prevent unauthorized access.
- Ensures data is secure during transmission or storage.
Why Is Cybersecurity Necessary?
Now that we are aware of a few terms related to cybersecurity, let us understand why it is vital:
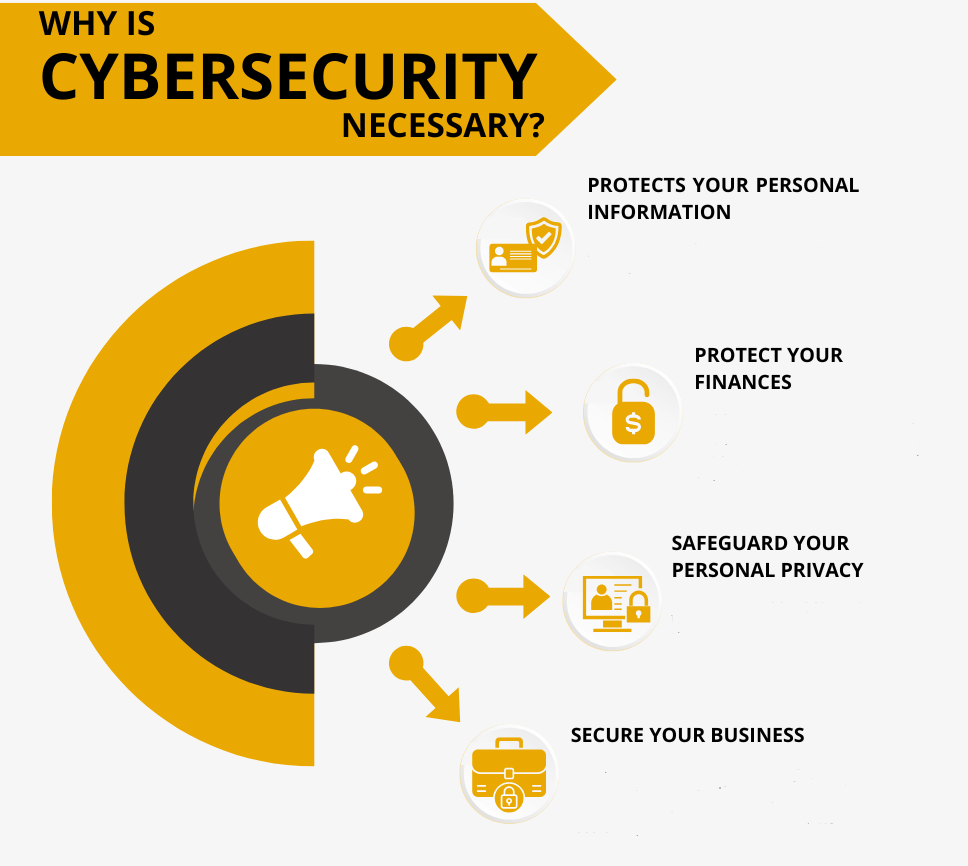
- Protects Your Personal Information: It prevents unauthorized access to passwords, financial information, and identity documentation.
- Protect Your Finances: It acts as a wall against scams, fraud, and other adverse cyber incidences that would otherwise deplete your accounts.
- Safeguard Your Personal Privacy: Given that your activities on the internet are time bombs, there is a need to keep them discrete.
- Secure Your Business: Companies and organizations utilize cybersecurity measures in order to minimize the chances of downtimes and loss of reputation and consumer trust.
Basic Types of Cyber Threats:
Cybercriminals have many tricks up their sleeves, so it’s important to be aware of the main types of attacks. Let’s highlight a few that are most alarming;
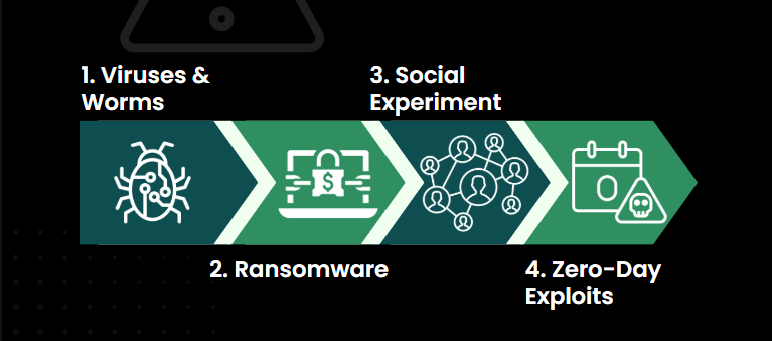
- Viruses and Worms: These bad software’s attach themselves to computers and could potentially wreak havoc to your files and several other computers in your network.
- Ransomware: This kind of malware is as bad as its name suggests, it places an order on which data you can access according to whether you pay the hackers or not.
- Social Engineering: People might be the reason why someone will steal your social security number or bank account details.
- Zero-Day Exploits: Such attacks use software vulnerabilities that even the owner of the specific software is not aware of.
The key is staying vigilant and using strong cybersecurity measures to protect yourself and your business. With the right knowledge, you can stay one step ahead of the bad guys.
Best Practices for Beginners
As a novice, what are the optimal strategies you should retain in mind to confirm that you don’t fall prey to any such assaults? Utilizing strong, complex passwords is indispensable, of course, but there are also some frequently overlooked approaches which can substantially improve your defenses with relatively small effort. Variation in sentence structure and length will help your writing appear more human and engaging to readers.
So, whether you are new to this field or just looking to stay safe online, consider implementing the following recommendations:
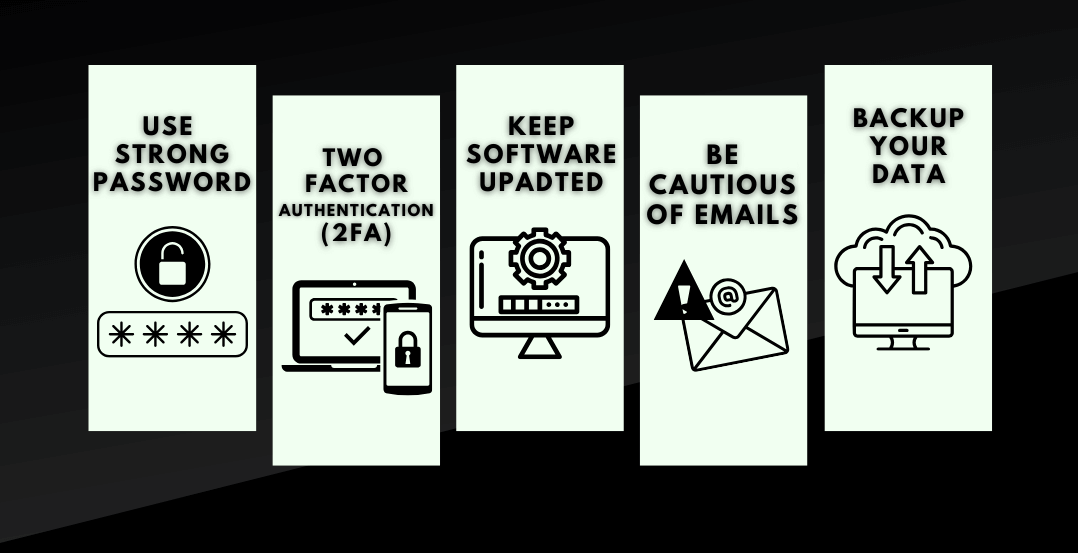
- Use Strong Passwords:
- Use long passwords containing a mixture of upper and lower case letters interspersed with numbers and symbols. Be sure to avoid easily guessed personal details such as your name or date of birth when setting credentials.
- Enable Two-Factor Authentication (2FA):
- Adds an extra layer of security by requiring a second form of verification.
- Examples: SMS codes or authenticator apps.
- Keep Software Updated:
- Educate yourself on current cyber threats and review available software updates regularly. Applying the latest patches and upgrades can help shield known vulnerabilities.
- Be Cautious of Emails:
- Exercise caution when opening email attachments or clicking unsolicited links, even if they appear to come from trusted contacts. Staying vigilant against phishing attempts is crucial.
- Back Up Your Data:
- Back up your files to the cloud or an external drive so your data remains secure even if disaster strikes.
- Learn to Recognize Scams:
- Stay informed about common cyber threats and how they operate. Protecting yourself with basic online safety practices does not require advanced technical skills – only a bit of awareness and diligence.
Career Paths in Cybersecurity
For those considering a career in cybersecurity, here are some popular roles one could pursue: the security analyst, ethical hacker, security engineer, and incident responder. Each plays a crucial part in defending against modern cyber threats.
- Security Analyst: The security analyst vigilantly monitors systems, searching for any signs of trouble. When suspicious activity is found, they work to determine whether a breach has occurred. It is a detail-oriented role where staying one step ahead of constantly evolving threats is key.
- Ethical Hacker (Penetration Tester): Ethical hackers, also known as penetration testers, take a more proactive approach. Their job is to find and exploit vulnerabilities before criminals can. By testing security controls, they help strengthen an organization’s defenses. It satisfies the desire to protect networks while indulging one’s technical curiosity.
- Security Engineer: Designing and implementing secure network solutions is the domain of the security engineer. Whether optimizing firewalls or implementing multi-factor authentication, they work to ensure only authorized access is granted. A strong technical foundation and creative problem-solving are must-haves for this role.
- Incident Responder: When attacks do manage to penetrate security, skilled incident responders step in. Their mission is to quickly contain damage and restore normal operations. Around-the-clock readiness is a necessity as breaches can occur at any time. Stress tolerance is important for this demanding work.
Final Thoughts
In summary, careers in cybersecurity offer fulfilling paths for those interested in technology and dedicated to safeguarding valuable data and systems. Persistent learning is key as threats evolve rapidly. But for individuals up for the challenge, the rewards of this meaningful work are plentiful.
Do you have a specific question about cybersecurity or need guidance on your learning path? Share your thoughts in the comments below!


